
An IT management methodology is defined to guide the way to manage and execute the various technology projects in the company.
The team has defined the steps to be followed and a logical order to effectively achieve the proposed objectives.
Flows, processes, responsible parties
The operation of the teams is based on developing activities, which are grouped to give processes, which interact with each other, as if they were gears, to make the area work, without being carried away by inertia.
The fundamental basis is the identification of activities, it may seem an easy fact, but it is not. It can be seen by looking at the number of things that must be done in a team and for lack of definition are not done or are done poorly, so it is not so clear its definition and identification.
The identification of processes and the definition of flows is intended to ensure that everything that is done in the IT team is identified and documented. For this purpose, the activities were identified in detail so that the limits of the processes can be defined.
Information security and privacy policies
The information security policies seek to serve as the main link to all activities that guarantee the proper handling of information, as well as to ensure the identification of information assets, evaluate and assess risks and take preventive and corrective measures to safeguard the integrity, availability and security of the same.
There are different processes and manuals that help to achieve this objective. Likewise, periodic evaluations of security, integrity and availability of the information, the correct execution of the processes and the disclosure of this information to the team and to third parties are carried out.
Information Security Management System (ISMS)
ISO 27001 is an international standard for securing and protecting physical and digital information. To this end, it provides a series of requirements to be met in order to manage the company’s information security.
Alto seeks certification to ensure that our technological products and their base processes comply with the security standard with emphasis on risk mitigation and increase the security of information, internal information or that of our customers and thus generate greater confidence of our customers in the use of our platforms.
Data Privacy
Alto takes reasonable steps to protect Personal Data provided through the Services against loss, misuse and unauthorized access, disclosure, alteration or destruction.
Certain technological security measures are implemented including encryption, firewalls and secure socket layer technology, however, these measures do not guarantee that information will not be accessed, disclosed, altered or destroyed by breach of such firewalls and secure server software.
Management and monitoring tools
In order to simplify and streamline the daily work of the team, different tools are used to organize, analyze and manage the different activities of the area. In addition, it is possible to monitor IT processes transparently and completely.
As an initial step, there is a tool such as Jira Service that allows the entire company to make technological requests and follow up on them, each request follows a management process within the IT area, the planning process is carried out in Jira. On the other hand, there are also communication and support tools such as Google Chat and intercom.
Monitoring and evaluation process
The management audit evaluates the degree of efficiency and effectiveness with which the available resources are managed and the objectives set by the team are achieved. It aims to improve the ability of employees to cope successfully with changes, aims to assess the strengths and weaknesses of the team or methodology, its leaders and corporate spirit: The strategic objectives are the focus of this audit.
For this purpose, different meetings and evaluations are carried out. This information, when analyzed, allows us to evaluate historical results, detect deviations, establish trends and produce yields. On the other hand, it evaluates the fulfillment of objectives and goals.
Architecture
An architecture defines the guidelines and techniques used to design and develop applications. The architecture provides a blueprint and best practices to follow when designing an application, so that you get a well-structured application.
In IT-developed application architecture, there are frontend and backend services. Frontend development refers to the user’s experience with the application, while backend development involves providing access to the actual data, services and other systems that enable the application to function.
An example of one of the products is shown below:
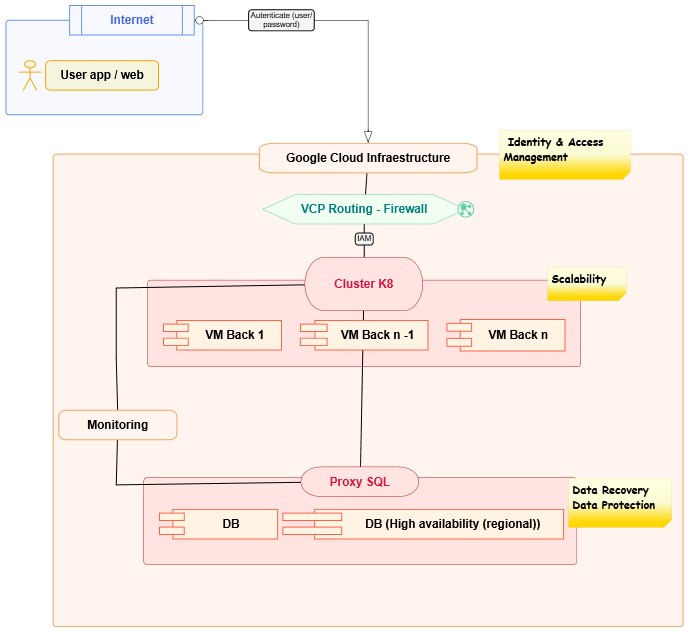
Project management
In IT each manager is in charge of applying technological, company, customer and product knowledge, using different skills, tools and techniques to define and manage the execution of various activities in order to meet the company’s requirements, as well as driving continuous improvement and product creation.
The main objective is to execute a process of planning, execution and control of a project focused on the construction or improvement of the functionalities of the different products, from its beginning to its conclusion, with the purpose of reaching a final objective in a determined period of time, with a determined cost and level of quality, through the mobilization of technical, financial and human resources.
Training
In order for the methodology to be an integral part of the processes carried out by the team, it is important to carry out different training cycles so that the team members are familiar with all the operating processes of the area, divided into different topics such as: best practices, security, management and development tools, products and architecture.
How much did you learn?
In the following link you will find questions related to the above explained.
Questionnaire Methodology This form is in Spanish, if you require translation you must submit the request at the following link: https://soporte-ti.atlassian.net/servicedesk/customer/portal/14/group/83/create/868
CLASSIFICATION: INTERNAL USE
Any printing or digital copy of the document is invalid. The user of the document must ensure that it is current before using it. This can be checked with the person responsible for the ISMS.