
Alto Alliance offers access from any device anywhere, to make use of the functionalities offered by the platform such as creating, assigning and performing tasks requested by a manager, optimizing task requests, offering the facility to show evidence of task completion or comments, thus obtaining an analysis of the compliance of store and local teams through immediate, scheduled or automatic tasks, visualizing their compliance and comparing by point of sale, as well as improvements to be made, as well as the possibility of verifying compliance KPIs.
The Alliance product is in charge of operational risk management, allowing to receive, analyze and visualize all the daily information happened or to happen in a store, this is achieved thanks to the assignment of tasks to the store members, as well as the possibility to report events happened in the store.
The Alliance product offers assistance to its clients, offering the facility to report any type of event occurring on the premises of up to seven categories in a daily operation and that are associated with a localized risk, being possible to attach evidence, comments, suspects, or additional data. In order to keep a record of what happened, and thus streamline the effectiveness and legal efficiency in the premises, offering ease to lawyers to perform an analysis through a legal flow in the event with legal cases. As well as providing recommendations to avoid similar events thanks to the patterns and analysis provided by Alliance, which analyze the data collected previously, looking for similarities and giving suggestions to prevent similar events from occurring.
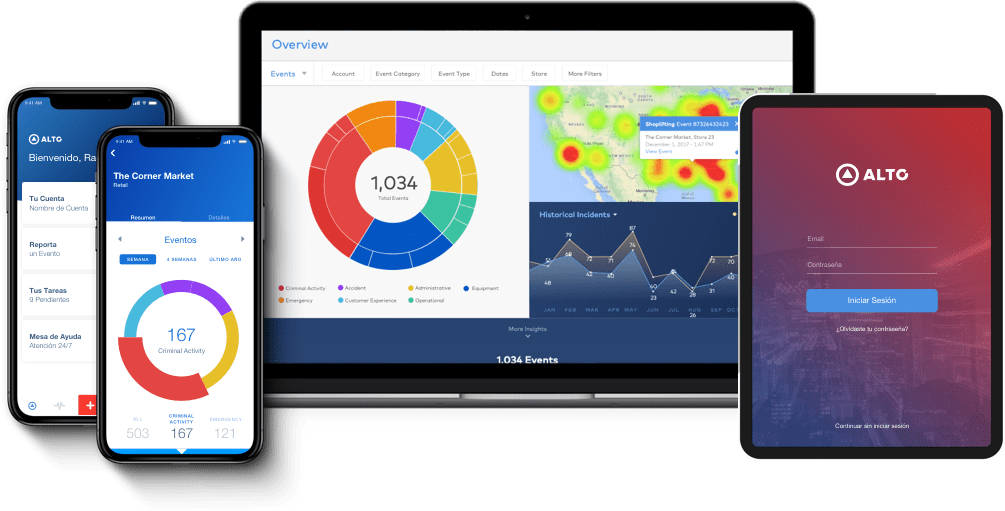
Functions
Event reporting
- Configurable reports for local needs, data cleansing, with an intuitive structure to create a report.
- Seven different categories of events can be parameterized for each client, depending on their needs:
- Criminal Activity
- Emergency
- Accidents
- Customer Experience
- Administrative
- Operational
- Equipment
- Increased knowledge and transparency of events or tasks requested at the site, on a daily basis.
- Creation of unstructured information, event management, information integration.
- It offers the facility to keep a record, analysis and legal flow for each event, facilitating follow-up by lawyers (if necessary).
- Event prediction models.
- Curious mode to visualize the events of all the users of the store.
- Events can be filtered in the web refactor viewer.
Assignment of tasks
- Dynamic and intuitive configuration when creating new tasks.
- Creation of tasks to the members of a local from anywhere in the world, with any Android, IOS or computer device.
- Alerts and notifications on tasks requested or completed.
- Three different types of tasks
- Push: Which are created with the purpose of requesting a task or reminder.
- Todo List: Common tasks to be performed by collaborators, it is a push type list of many tasks (Requests), in a single request.
- Checklist: Consists of a series of questions type list, which once completed, will throw a matrix of answered, not answered and does not apply, in order to conduct a survey on a check on the premises.
- Task estimation models to optimize and recommend assignments.
- Automatic tasks for daily and recurring tasks of the facility operation.
- Tasks can be filtered in the web refactor viewer.
Discovery (Reports)
- Online access to information, results and analysis of events and tasks, offering multi-layer dashboards (events, people, places, accounts).
- Dynamic search, pattern scoring, digital band integration, band linking.
Legal Cases
- Creation of legal cases with evidence, suspects, and information relevant to the case.
- Coordination of legal cases for optimal follow-up.
- Support in the legal flow of each event, through the coordination of events. Which will guide the user in the legal case.
- Easy access of lawyers to the cases of each event.
- Legal cases can be filtered in the web refactor viewer.
Books
- Attachment of evidence and relevant information for each store.
- Maintain a record for all Alto members.
- Creation of records of type Text, date, attachment or numeric.
Stores
- General information of each store and its account
- Scheduling and/or creation of touchpoints relevant to the store with the function to report on Visits, event information, meetings, evidences and documents.
- Stores can be filtered in the web refactor viewer.
Call center
The call center functionality seeks to advise, validate and receive events that contain a person in charge, a location, the assigned event account and description.
More information This information is in Spanish, if you require translation you must submit the request at the following link: https://soporte-ti.atlassian.net/servicedesk/customer/portal/14/group/83/create/868
Architecture

Infrastructure
To achieve this goal, a computationally correct platform is necessary, so ALTO Alliance is developed under a state-of-the-art computational architecture that combines the power of cloud computing (Google Cloud Platform (GCP)), the flexibility of microservices models and the scalability of Kubernetes technology on an analytical sheet developed on R and Python, then, the system architecture is presented. This architecture generates an ecosystem with a series of characteristics which are highlighted below:
- Stability: System based on Load Balancing and Dockers, this allows better management of expected and unexpected processes, it also allows distributing user traffic across multiple instances and thus reduces the risk of experiencing performance problems. Scrum development methodology, which allows for better development management and risk mitigation. Hybrid database, which allows for efficient data management, both for transactional, columnar and multidimensional problems that we face within the smart data model.
- Scalability: Microsite structure (microservices and micro front ends), this allows focused growth and a platform based on modules. Columnar database allows better response latency and therefore more explanatory information. Structure based on big data model to improve data frequency and/or volume.
- Security: GDPR-based methodology for compliance with data management and privacy policies. Tokenization system based on Blockchain to ensure data security not only in the system. Encrypted database to ensure data security.
- Technology: Continuous Development Model for better response in releases and the possibility of customized and staggered developments. Profiling scheme for a better model of customization of views and/or functionalities as well as a unique experience per user type. Data Cleaning is a technique focused on data quality which results in more accurate models and conclusions. Structure of functional (linear) and non-functional (deep learning, AI, etc) models for risk estimation and calculation of prescriptive actions allowing better estimation of models based on the data. Multidimensional data structure for better data interpretation and the possibility of real-time access to aggregated information.
- Speed: Hybrid DBs to improve processing frequency or processing distribution. Multi-tenant schemes for better and greater user management. Lists and processes in elasticsearch for better performance.
- Monitoring: system that provides visibility into performance, uptime and overall application status.
Physical and technological information security management
It is worth mentioning, within the system, its architecture based on a scalable and reliable infrastructure. Based on a cloud architecture strongly related to a microservices model both in the front-end and back-end, ALTO Group systems are scalable and high performance, as well as focused on information security based on different tools where it stands out; monitoring, user authentication and encryption and / or tokenization of information depending on the sensitivity of it. Our system controls access by role, account and store, restricting unauthorized access to information not related to your user, in addition, access to information is controlled at the user level and the connection to gcloud (servers and databases). Also, access to network devices is managed through a firewall, authentication is done with Cloud Identity and Access Management (Cloud IAM), which allows managing identity and access control by defining who (identity) has what access (role) to what resource. On the other hand, Alto has defined data privacy policies, which can be consulted in each application and must be accepted in order to use them, and each company collaborator and supplier has signed confidentiality agreements. In addition, the user of the system must know and accept the data privacy policies in order to make use of it.
The documents are shown below:
- Security
- Product description
- Discovery
- Manual web version
- App version manual
- Web refactor version manual in English (User)
- Manual web refactor version in English (Backoffice)
- Web refactor version manual (User)
- Manual web refactor version (Backoffice)
- Administrators manual (User, checklist, todolist)
- Process Manager Manual
- Frequently asked questions App ES
- Frequently asked questions App EN
- Profile matrix
- Frequently Asked Questions
- Versioning
- Service level agreements
- JMeter Manual
- RoadMap
Some of this information is in Spanish, if you need a translation you must request it at the following link: https://soporte-ti.atlassian.net/servicedesk/customer/portal/14/group/83/create/868
Below are our support videos:
Some of this information is in Spanish, if you need a translation you must request it at the following link: https://soporte-ti.atlassian.net/servicedesk/customer/portal/14/group/83/create/868
How much did you learn?
In the following link you will find questions related to the above explained.
Alliance Product Questionnaire This form is in Spanish, if you require translation you must submit the request at the following link: https://soporte-ti.atlassian.net/servicedesk/customer/portal/14/group/83/create/868
CLASSIFICATION: INTERNAL USE
Any printing or digital copy of the document is invalid. The user of the document must ensure that it is current before using it. This can be checked with the person responsible for the ISMS.